Introduction
This is my write-up for TryHackMe's Blog Room.
Enumeration
Using nmap, I saw that this box is running SSH and HTTP and SMB.
Using nmap, I saw that this box is running SSH and HTTP and SMB.
Checking for shared SMB folders, I found an interesting one:
I then checked the interesting folder:
I first checked tswift.mp4 but found it to be a spoofed music video. Watch it if you don't believe me.
check-this.png looked promising. But it turned out to be just a regular barcode, or is it? Uploading the image file to an online barcode reader, I see that it contained a URL:
Turns out the URL is just a YouTube video:
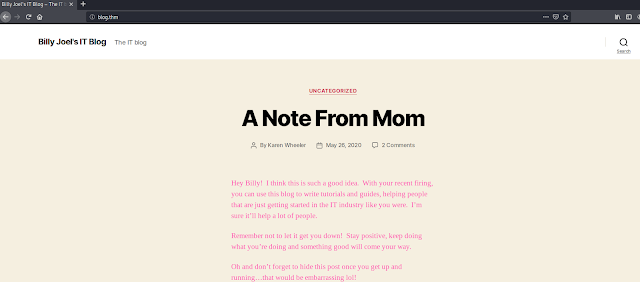
Lastly, I then checked Alice-White-Rabbit.jpg.
So it turns out checking the SMB share is indeed a rabbit hole.
I then proceeded to check the Web Site. (Do note that according to the instructions you need to add the site to your /etc/hosts file to work properly)
Scrolling further down, I find it is running WordPress:
Running wpscan, I find it is running WordPress 5.0.
Another run of wpscan reveals the users.
A 3rd run of wpscan revealed the password for one of the users.
Exploitation
I saw that Metasploit already had a number of available exploits for Wordpress.
Checking the WordPress Crop-Image Shell Upload exploit, I found that it only required the username and password for the site (which I already had!).
Setting the necessary values and running, I got a shell:
Privilege Escalation
Checking for SUID permissions, I found an interesting file:
Checking the properties, I see that it is owned by root:
But simply running it leads nowhere.
Running gdb, I found that it runs getenv function.
According to the man page, this function searches the environment list to find an environment variable name:
So going back to gdb, I needed to check what the function is searching for. Looking at memory location 0x559ae57c17f4, I find:
Converting these values, I see that what environment variable it is searching for.
From the disassembled code, I see that it only checks for the presence of the environment variable. It does not matter the type (whether integer, string, etc). So I can just export a variable and run the program.
And I got root privileges!
And the flags can be found here:























No comments:
Post a Comment