Introduction
This is my write up for TryHackMe's Mindgames Room.
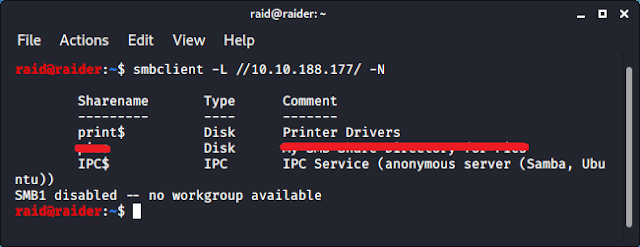
Enumeration
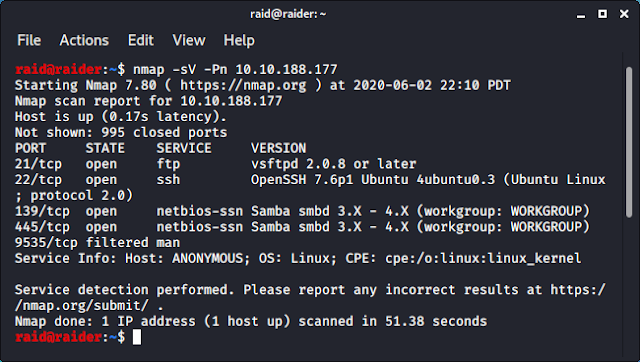
Nmap scan shows that both HTTP and SSH are running.
Looking at the webpage, I see what looks like BrainF*ck encrypted text.
Going to dcode.fr, I see that decoding the "Hello, World" code results to a simple Python print statement.
And that the "Fibonacci" code is Python code that prints out the Fibonacci Sequence:
If that being the case, then it might be possible to inject code!