TryHackMe write-up: Startup
TryHackMe write-up: Brute It
Introduction
Enumeration
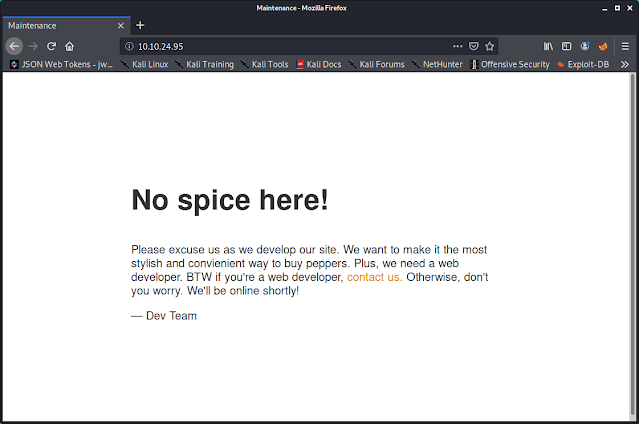
TryHackMe write-up: The Marketplace
Introduction
Enumeration
TryHackMe write-up: Revenge
Introduction
After hacking Billy's website, he tracks us down and sends us the following note.
Enumeration
Using nmap, I saw that this box has 2 ports open.
Checking port 80, we see that it is hosting the company's website:
I wanted to check the products page so I checked the first product they were selling.
Funny though is that the product id is listed as part of the URL. In this case, it is http://10.10.151.163/products/1. I then checked what would happen if I typed in a non-existent product id, say 999:
TryHackMe write-up: Res
Introduction
This is my write-up for TryHackMe's Res Room.
Enumeration
Using nmap, I saw that this box 2 ports open.
Checking port 80, I found that it is running Apache.
TryHackMe write-up: Poster
Introduction
This is my write-up for TryHackMe's Poster Room
Enumeration
Using nmap, I saw that this box has several ports open.
TryHackMe write-up: Jacob the Boss
Introduction
This is my write-up for TryHackMe's Jacob The Boss Room
Enumeration
TryHackMe write-up: Bolt
Introduction
This is my write-up for TryHackMe's Bolt Room
Enumeration
TryHackMe write-up: Tartarus