Introduction
This is my write-up for TryHackMe's Tartarus Room.
Enumeration
Using nmap, I saw that this box is running FTP, SSH and HTTP.
Checking the FTP, I found that there were some "hidden" directories. Those directories named "..." would have been hidden if one simply checked using the "ls" command.
Checking the file yougotgoodeyes.txt, it looks like it points to a secret directory.
Going to the directory using my browser, I came upon a login page.
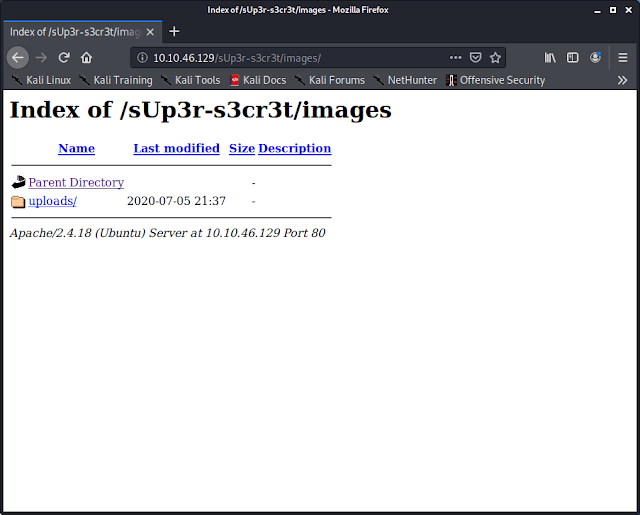
Checking the robots.txt file, I see that there's another hidden directory.
Checking this directory using my browser, I saw what looks to be files that can be used to login to the target.
The file userid looks to be a list of users.
While the file credentials.txt seem to be a list of possible passwords.
Exploitation
Running hydra, I was able to get a matching userid and password credentials to logon to the website.
On logging in, I saw a file upload page.
Running dirb, I found another directory inside the secret directory.
And checking that directory, I found another one.
Going back to the file uploader home page, I uploaded a php-reverse shell I found from pentestmonkey.net. Going to the uploads directory and selecting the php file I just uploaded, I then get a reverse shell.
Privilege Escalation
Checking /etc/crontab, I saw that a python script was ran every 2 minutes.
Given that I had write access to cleanup.py, I decided to replace this with a reverse-shell python script.
After 2 minutes, my netcat listener received a shell connection.
















No comments:
Post a Comment