Introduction
This is my write-up for TryHackMe's Bolt Room
Enumeration
Using nmap, I saw that this box has ports 22, 80, and 8000 open.
Checking port 80 using my web browser, I find that it is running Apache2.
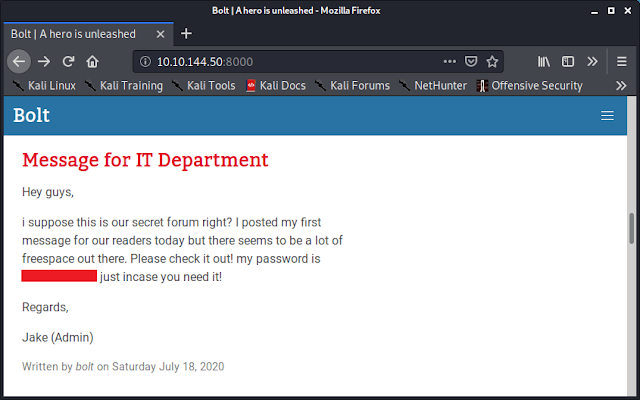
Checking port 8000 on my browser, I find that it is running Bolt CMS.
Exploitation
Scrolling through the page, I saw what may be a password.
And scrolling further, I found a username that may go with it.
Searching metasploit I found that there's an Authenticated Remote Code Execution exploit available. Good thing I found credentials. Setting the proper options as follows:
And running the exploit:
I got root!







No comments:
Post a Comment