Introduction
Enumeration
Using nmap, I found that this box had 3 ports open.
The webpage looked like it was still under development.
I then ran gobuster and found a hidden folder.
Looking at the files directory, I saw the following:
Going back to the ftp service, I tried logging in via anonymous user.
Exploitation
Checking the ftp service, I found that I could upload a php file to the /ftp folder. I tried uploading the php reverse shell script found at
pentestmonkey.net.
Looking back during the enumeration phase, I recalled that there was a folder named ftp inside the website's files directory. I was able to access the uploaded php file.
Checking the netcat listener I opened prior to accessing shell1.php, I found that I now have a shell back to the target.
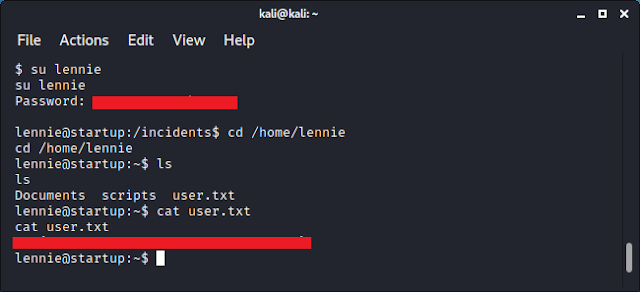
Checking the directory, I found that there is a file named recipe.txt. This contained the answer to the first question.
Looking back at the files and folders shown above, I saw an "incidents" folder. On looking further, it contained a pcap file. I was then able to transfer this file to my attacker machine via ftp.
Checking the traffic, I found that another hacker had a shell (same as what I had), and was trying to run sudo. However, the password used would not work.
But maybe the password would work for a different user? I tried switching to a different user and the password was correct for said user.
Privilege Escalation
Finding a way to escalate privilege was a bit tricky. I couldn't run sudo as the current user and passwords weren't available at accessible files.
Checking the files on the scripts folder, I found a script file and a text file. Planner.sh wrote something to startup_list.txt and then called /etc/print.sh. The thing is, after about a minute, startup_list.txt was modified by root.
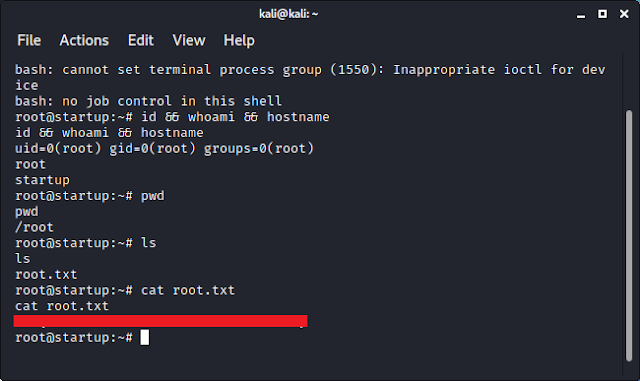
Given that the text file was modified by root, it means that there must be another root process (maybe a cron job or something) that calls planner.sh. However, given that I didn't have write privileges to planner.sh, I had to write somewhere else. It's a good thing that I had write permissions to /etc/print.sh. I then overwrote it to run a reverse shell back to my attacker machine.
After a while, I found that the target has connected back to my netcat listener and I had root permissions.














No comments:
Post a Comment