Introduction
This is my write-up for TryHackMe's Anonymous Room
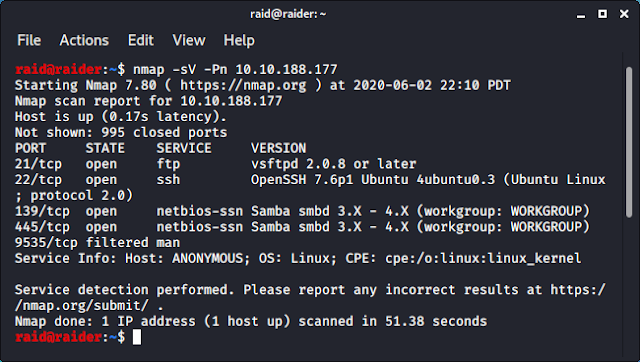
Using nmap, we see that FTP, SSH and SMB ports are open.
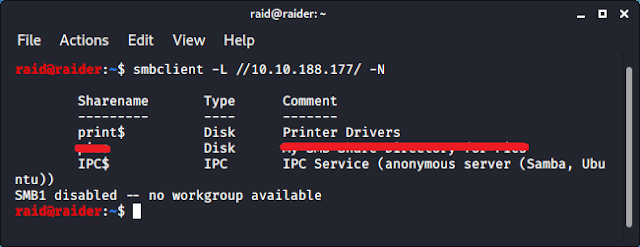
One question asks for the name of the share. We can use smbclient to do so.
Exploitation
Trying to go through the SMB route seemed like a rabbit hole for me. An easier method was to check FTP.
We see that FTP allows for anonymous access. Digging deeper, we also see that there is a directory named "scripts".
We see that the script clean.sh has read and write and execute permissions! Looking at the script further:
We then replace it with the following script:

Privilege Escalation
Running find / -perm -u=s 2>/dev/null, we see that env has its SUID bit set.
Checking GTFOBINS, we see that it can be used to escalate our privileges!





No comments:
Post a Comment