Introduction
This is my write up for TryHackMe's Mindgames Room.
Enumeration
Nmap scan shows that both HTTP and SSH are running.
Looking at the webpage, I see what looks like BrainF*ck encrypted text.
Going to dcode.fr, I see that decoding the "Hello, World" code results to a simple Python print statement.
And that the "Fibonacci" code is Python code that prints out the Fibonacci Sequence:
If that being the case, then it might be possible to inject code!
Exploitation
Through some trial-and error, I was able to check the current running directory. I'm not sure but 1-liner Python code seems to be easier.
Encoding the following line:
I was able to get a shell.
Privilege Escalation
Running linpeas.sh, I find that openssl has cap_setuid.
Checking GTFOBins, it turns out that loading a library onto openssl can be used for privilege escalation.
A Google search brought me to the following OpenSSL Blog
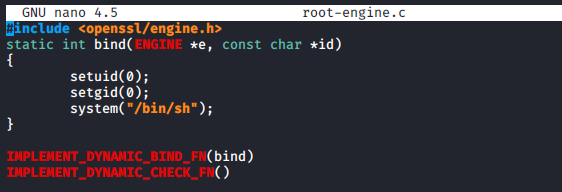
It basically describes how to write and build your own OpenSSL engine!
So then, I wrote the following code:
And then compiled it as follows:
Sending it over to the target machine and loading it as shown in GTFOBins, I was able to gain root access.













No comments:
Post a Comment